what to check for data integrity in spreadsheet
If your company'southward data is altered or deleted, and you take no manner of knowing how, when and by whom, it can have a major impact on data-driven business organization decisions. This is why data integrity is essential. To understand the importance of data integrity to a company'south bottom line, let us examine what it is, why it'southward significant, and how to preserve it.
What is Data Integrity?
Data integrity refers to the reliability and trustworthiness of data throughout its lifecycle. It can draw the state of your data—due east.k., valid or invalid—or the process of ensuring and preserving the validity and accuracy of data. Error checking and validation, for example, are mutual methods for ensuring data integrity equally part of a process.
Want more insight into data security trends? Download our in-depth data breach statistics report.
What is the Difference Between Data Integrity and Data Security?
Data integrity is non to be confused with data security. Information security refers to the protection of data, while data integrity refers to the trustworthiness of data.
Data security focuses on how to minimize the risk of leaking intellectual property, business documents, healthcare data, emails, merchandise secrets, and more. Some data security tactics include permissions management, data classification, identity and admission direction, threat detection, and security analytics.
Why is it Important to Maintain Information Integrity?
Imagine making an extremely of import business organization determination hinging on data that is entirely, or even partially, inaccurate. Organizations routinely make data-driven business decisions, and information without integrity, those decisions tin accept a dramatic effect on the visitor'southward bottom line goals.
A new study from KPMG International reveals that a large bulk of senior executives don't have a high level of trust in the way their arrangement uses data, analytics, or AI.
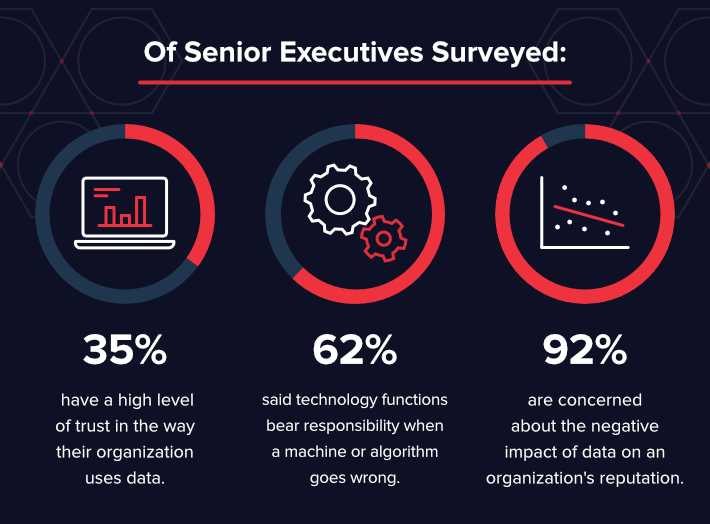
Simply 35% say they have a high level of trust in the manner their organization uses data and analytics. 92% are concerned about the negative impact of data and analytics on an organization's reputation. What's more, 62% of senior executives said applied science functions, non the C-level and functional areas, acquit responsibility when a motorcar or an algorithm goes wrong.
Organizations need to go through the motions of preserving data integrity in order for C-level executives to brand proper business organisation decisions.
Information Integrity Threats
Data integrity tin be compromised through human error or, worse nonetheless, through malicious acts. Data that'due south accidentally altered during the transfer from i device to another, for example, can be compromised, or even destroyed by hackers.
Common threats that tin alter the state of data integrity include:
- Human mistake
- Unintended transfer errors
- Misconfigurations and security errors
- Malware, insider threats, and cyberattacks
- Compromised hardware
So how do you know when your information has integrity? You accept to look at the following features:
Retrievability and accessibility – Information technology'southward of import to accept accurate data in the proper locations at the right time when anyone is working on projections, a deal, or presentation. Without proper and easy access and retrieval, it can exist detrimental to the business, yielding the way for your competition to win.
Traceability –Today, you lot can trace every touchpoint you make with a prospect or client. How? With a information bespeak. The data tin can inform decision makers, highlight ruby-red flags, deficiencies, or limitations. Make certain these touchpoints are accurate.
Reliability – Having reliable, consistent business metrics against visitor goals and the competition is what will take an organization to the tiptop.
How to Preserve Data Integrity [Checklist]
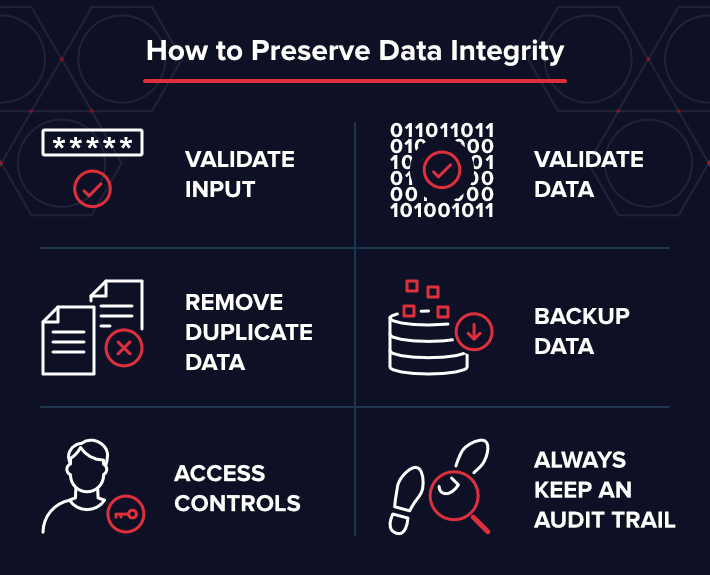
The data integrity threats listed above besides highlight an aspect of data security that can help preserve data integrity. Use the post-obit checklist to preserve information integrity and minimize risk for your system:
- Validate Input:When your data set is supplied past a known or unknown source (an finish-user, another awarding, a malicious user, or whatever number of other sources) you should crave input validation. That data should be verified and validated to ensure that the input is accurate.
- Validate Data: It's disquisitional to certify that your information processes haven't been corrupted. Place specifications and fundamental attributes that are important to your organization before you validate the data.
- Remove Indistinguishable Information: Sensitive data from a secure database can easily detect a domicile on a document, spreadsheet, email, or in shared folders where employees without proper access tin can see it. It'southward prudent to make clean up stray information and remove duplicates.
Smaller companies without a dedicated staff will find that these tools tin can assist them make clean up duplicate files on a difficult drive or cloud.
- Clone Files Checker
- Indistinguishable Images Finder
- Like shooting fish in a barrel Duplicate Finder
- Duplicate Cleaner
- CCleaner
- DoubleKiller
- WinMerge
For Windows Servers: Use the Data Deduplication feature to clean upwardly cloned files. As well try the File Server Resources Director to remove stray files.
- Support Data: In addition to removing duplicates to ensure data security, data backups are a critical part of the process. Backing up is necessary and goes a long mode to forestall permanent data loss. How often should you exist backing up? Equally oft as possible. Keep in mind that backups are critical when organizations get striking with ransomware attacks. Merely brand sure that your backups aren't also encrypted!
- Access Controls: We've made the case higher up for input validation, data validation, removing duplications, and backups – all necessary to preserve data integrity. Let's not rule a few pop data security all-time practices that can also lend a paw or two: access controls and an inspect trail! Individuals within an organization without proper access and with malicious intent tin can exercise grave harm to the data. What's worse, an outsider impersonating an insider can likewise exist detrimental. Implementing a to the lowest degree privilege model – where only users who demand access to data become admission – is a very successful form of admission control. What's often overlooked is concrete access to the server. The about sensitive servers should be isolated and bolted to the floor or wall. Only individuals who admission should have an access central – ensuring that the keys to the kingdom are kept secure.
- Always Keep an Audit Trail:Whenever there is a breach, information technology'southward critical to data integrity to be able to track down the source. Frequently referred to as an audit trail, this provides an arrangement the breadcrumbs to accurately pin indicate the source of the problem.
Typically, an audit trail has the following:
- Inspect trails need to be automatically generated
- Users should not have access to or the power to tamper with the audit trail
- Every consequence – create, delete, read, modified – is tracked and recorded
- Every event is also aligned to the user, so you know who accessed the information
- Every event is time stamped and then that you know when the event took place
Data Integrity Empowers Decision Makers
Not too long ago, information technology was difficult to collect data. However, today it'south no longer an effect. In fact, we're able to collect so much information, the responsible thing to do is to preserve data integrity. That way, management can confidently brand data-driven decisions that steer their visitor in the right direction.
Interested in more data on data integrity? Have a listen to our podcast with Ann Cavoukian on GDPR and Admission Control or browse through our article on The Difference Between IAM's User Provisioning and Data Access Management.

Cindy Ng
Cindy is the host of the Inside Out Security podcast.
Source: https://www.varonis.com/blog/data-integrity
0 Response to "what to check for data integrity in spreadsheet"
Post a Comment